热门搜索:
应用安全
- 应用安全
- 代码卫士
- 开源卫士
- 漏洞扫描系统(SecVSS)
云安全
智慧城市
- 咨询规划
- 内生安全框架
- 网络安全体系规划服务
安全运行保障
- 重保服务
- 重要时期安全保障服务
安全应急响应
- 安全应急与事件分析
- 应急响应服务
安全咨询规划
- 安全咨询规划服务
- 等保合规咨询服务
- 工控安全咨询规划服务
- 信息安全管理咨询服务
-
安全产品
- 终端安全
-
网络安全
- 防火墙与网关
- 网络隔离
- 网络入侵检测与防御
- 上网行为管理
- 其他
-
云安全
- 云计算安全
- 服务器安全
- 网站云安全
- 云安全服务平台
-
应用安全
- 应用安全
-
数据安全
- 数据安全防护
- 数据流通安全
- 个人信息保护
- 安全运营
- 安全监管
-
工业安全
- 工业安全防护
- 工业安全检测审计
- 工业安全运营管理
- 工业安全实验室
-
电子取证
- 终端取证
- 网络空间取证
- 现场勘查
- 采集与数据分析
- 综合取证
- 鉴定服务
- 信创
- 密码安全
-
解决方案
- 专项解决方案
- 行业解决方案
- 云安全
- 智慧城市
- 通用解决方案
-
咨询规划
- 咨询规划
-
安全服务
- 安全实战攻防
- 安全集成实施
- 安全运行保障
-
安全应急响应
- 安全应急与事件分析
- 安全教育
-
安全咨询规划
- 安全咨询规划服务
- 技术支持
- 投资者关系
- 安全能力
- 合作共赢
- 关于我们
- 登录


 立即拨打
立即拨打



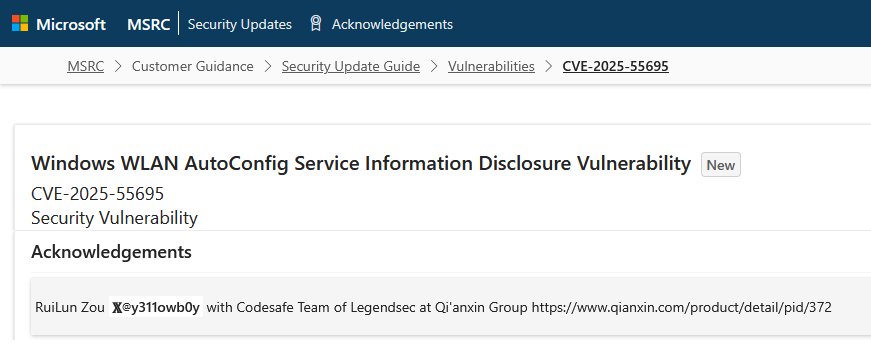
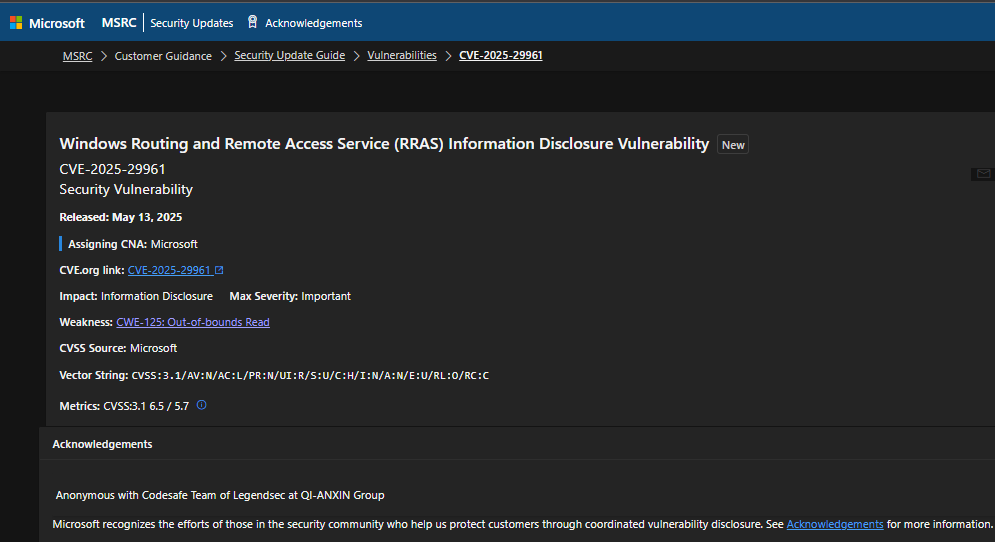
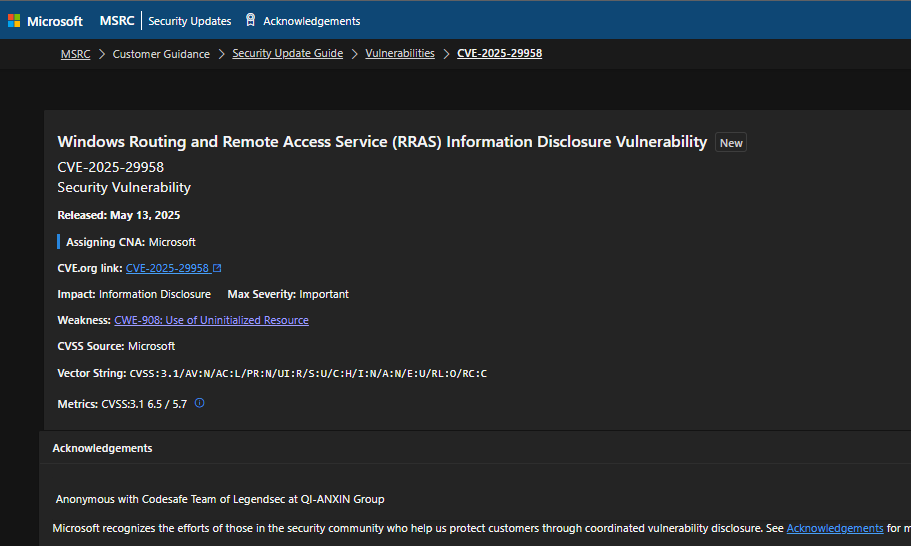
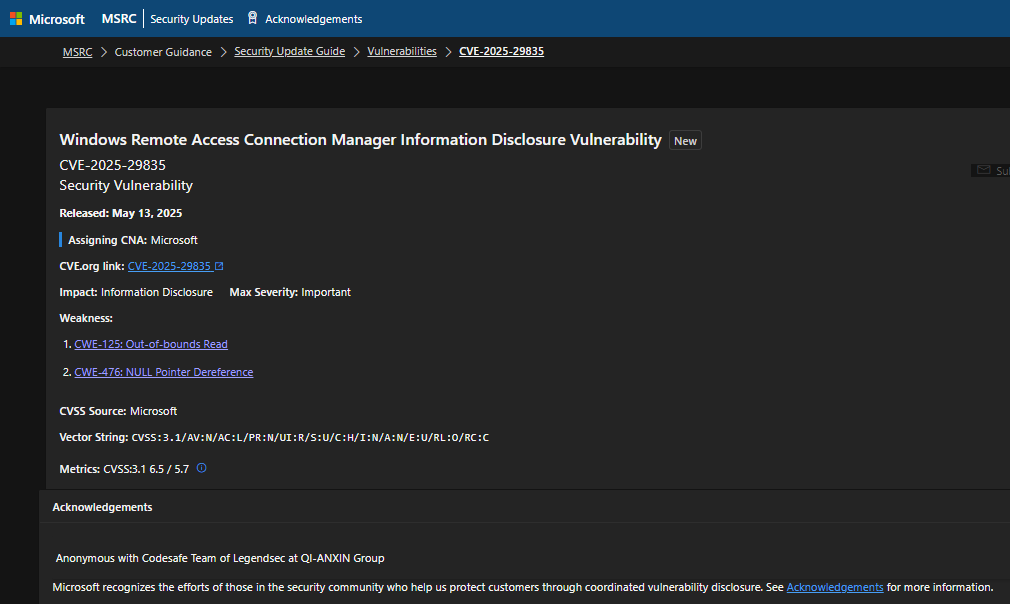
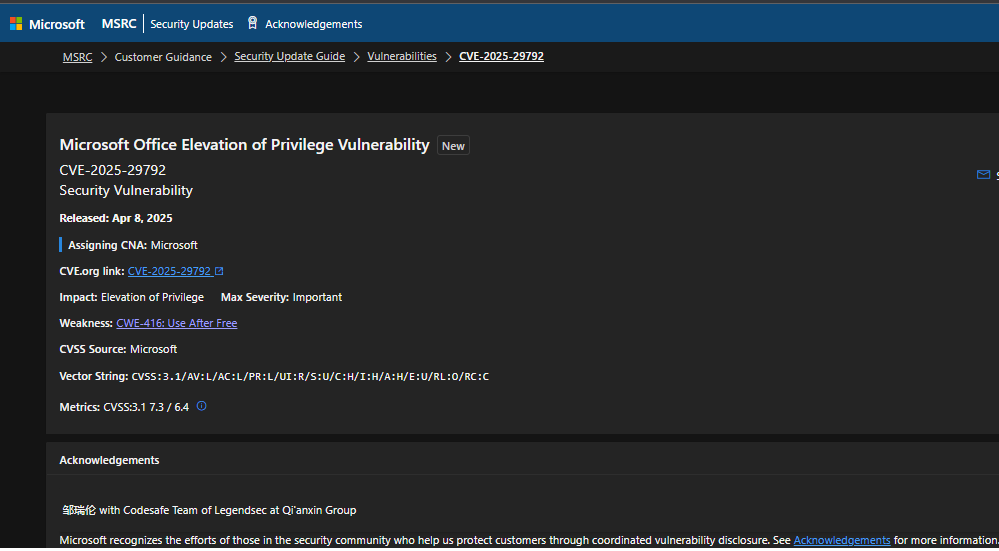
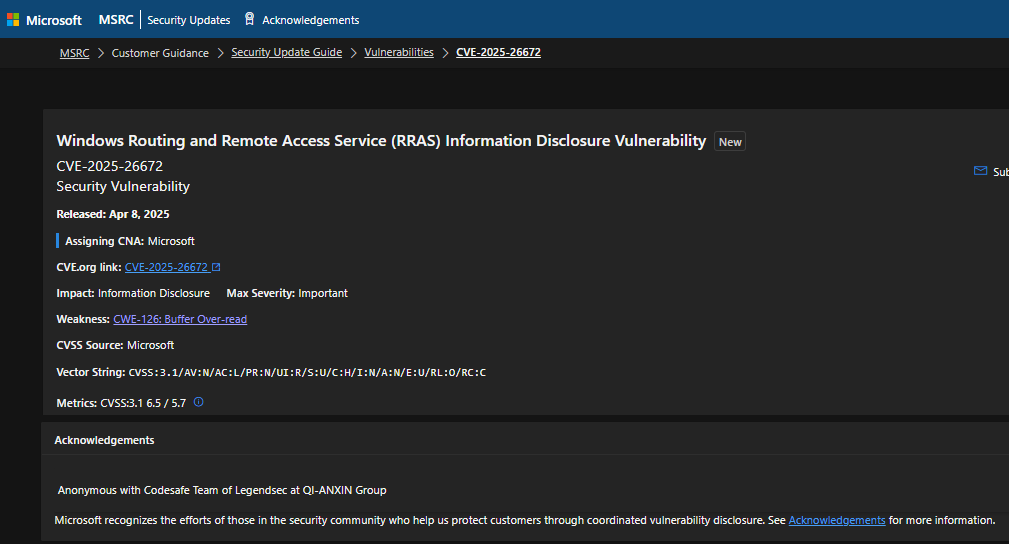








 京公网安备11000002002064号
京公网安备11000002002064号