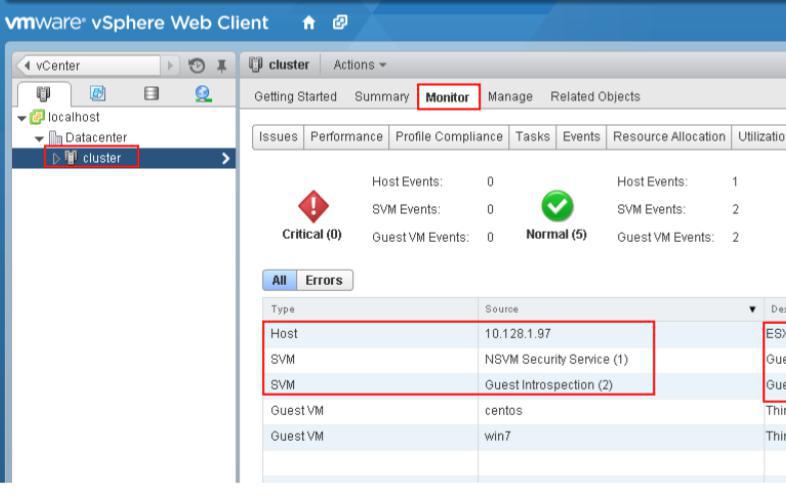
1)First Login Vcenter Vsphere Web Client, select “cluster” in the page of “ local
host and cluster”, then enter into the page of “ Monitor-Guest Introspection”, and check if the description and
status of host, NSVM Security Service, Guest Introspection are correct.
2)Then according to the VM operating system for troubleshooting.
WindowsVM
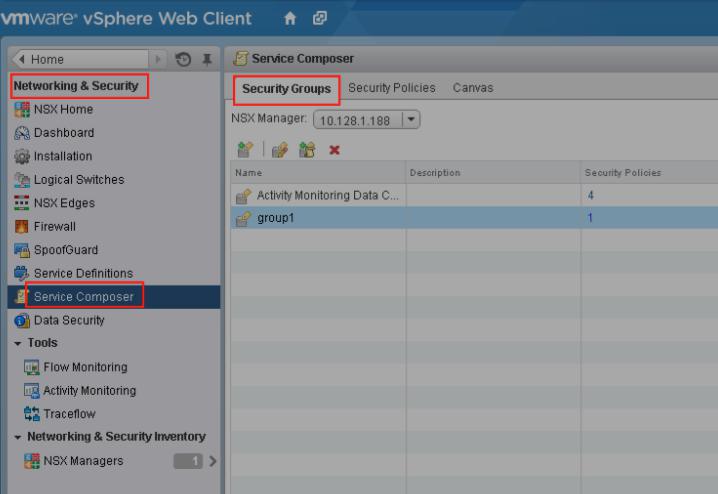
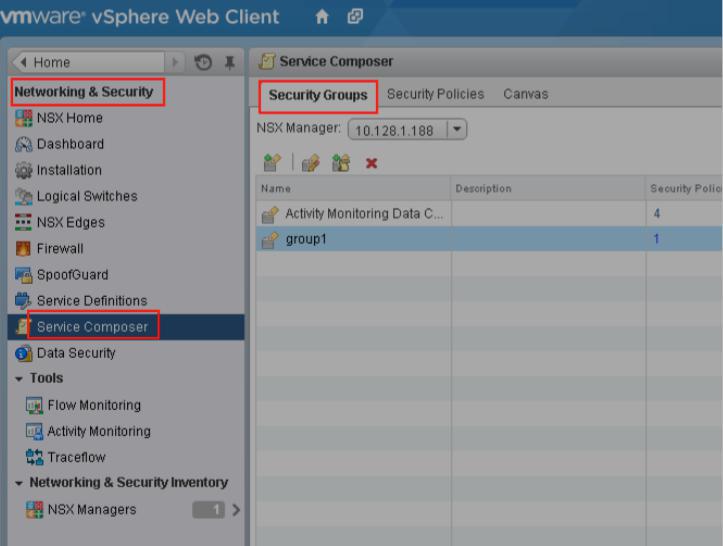
a)Enter into the page of “ Networking & Security” –“Service Composer “–“Security Groups” in vCenter vSphere Web
Client, and click the value of VM in the Security Groups, then check if the windows VM is included in the security
groups in the dialog box.
b)Check if the configuration applied in this windows VM have turned on “ Real-time protection”. Login management
center, enter into the page of “ Asset Management- VM/Terminal” to check the status of “ Real-time protection”. If
the status is not “ Real-time protection on”, please change the security configuration matched and turn on “ Real-
time protection”.
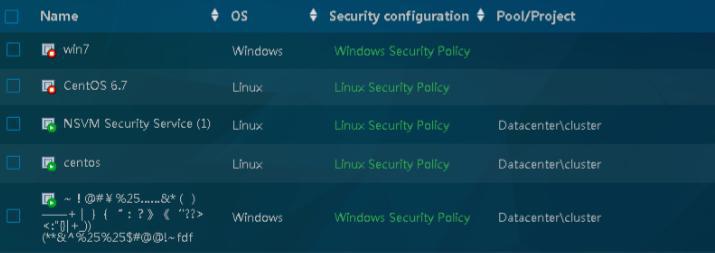
c)Then check if this VM has already installed with VMware tools and “NSX File Introspection Driver” by custom
installation.
d)In the command line of VM to run “scquery vsepflt” and check if the service is existing. The following picture1
shows that is normal; the picture2 shows the service is unavailable.
Service is normal:
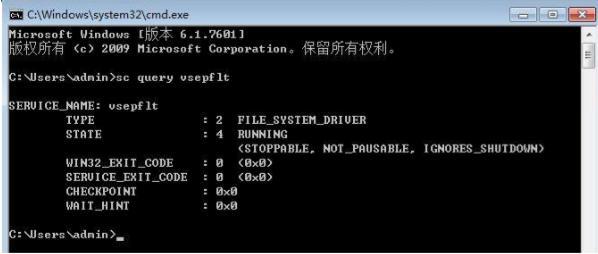
Service is unavailable, please install VMware tools again:
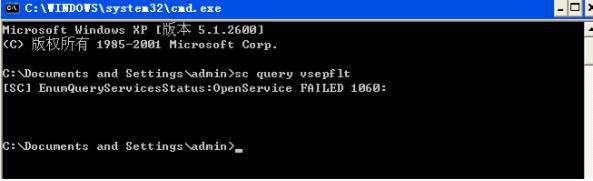
e)If the service is unavailable, please install VMware tools again, and select the driver of NSX File
Introspection under “ VMCI driver” by custom installation. After installation, reboot VM and make sure
that VMware tools has been installed.
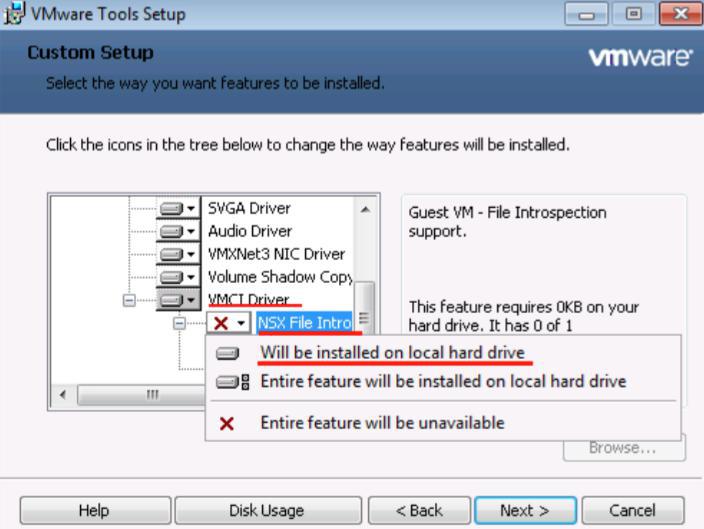
Versions before vSphere 5.5 U2 should search“VMCI driver”, and select to install “vShield Drivers”to local disk
Find “VMCI driver” and select “vShield Drivers” to install it in local disk.
PS:If there is not “ NSX File Introspection Driver” or the option of “ vShield Drivers” like the picture above in
the dialog box of “VM ware Tools”, which means that the version of VMware Tools is old, you need download the new
version of VMware Tools. And this is the website:
https://packages.vmware.com/tools/esx
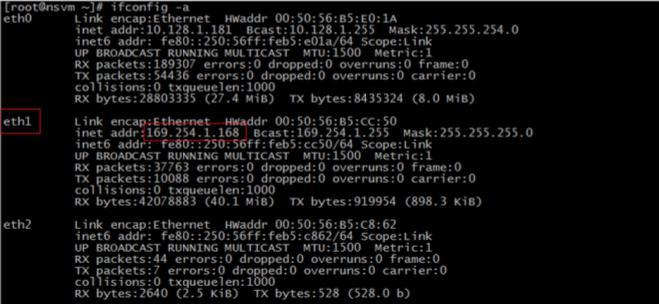
f)Check the security VM of host. Login this security VM through console or SSH and execute the command of
“ifconfig-a”, and the IP of eth1 is as following:
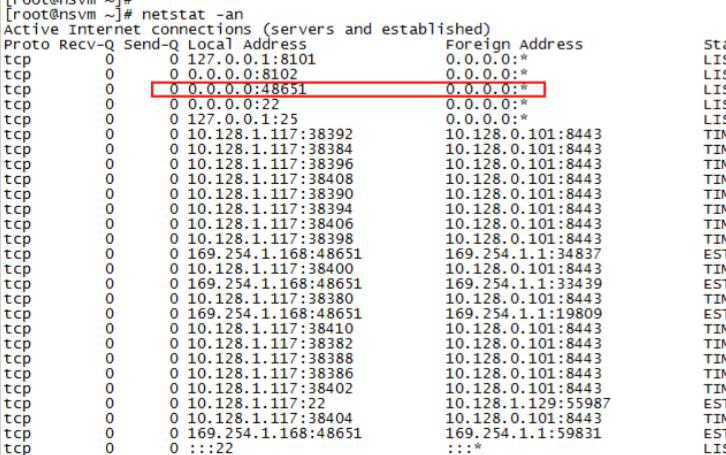
g)Test security and the communication of VM. You can ping the IP169.254.1.1 of vmsevice-nvmsec-pg from security
VM. Security process monitors TCP48651 port of this machine. If the protected VM is enabled, it will connect with
local 8000 port.
LinuxVM
a)Make sure if the operating system of linux VM is supported, refer to
Appendix-Linux OS lists of support.
b)Enter into the page of “ Networking & Security”- “Service Composer”-“Security Groups “ in vCenter vSphere Web
Client, click the value of “VM” lists in the page of security groups, then check if the Linux VM is included by
security groups in the dialog box.
c)Check if the configuration applied in this linux VM have turned on “ Real-time protection”. Login management
center, enter into the page of “ Asset Management- VM/Terminal” to check the status of “ Real-time protection”. If
the status isn’t “ Real-time protection on”, please change the security configuration matched and turn on “ Real-
time protection”.
d)Enter into the command line of linux VM, check through the command of service vseped status if the service
status of vseped is correct, and the normal is running.


 立即拨打
立即拨打



















 京公网安备11000002002064号
京公网安备11000002002064号